How to Use the Merkle Root to Enhance Security in IoT Devices
This blog post delves into Merkle Root's critical role in enhancing the security of IoT devices. As IoT devices become increasingly prevalent in smart homes and industrial settings, their constant connectivity and limited processing power make them vulnerable to cyber threats. The post explains how Merkle Root, a robust cryptographic tool, helps maintain data integrity and verify information without relying on central servers or complex infrastructures. The article covers critical applications of the Merkle Root in IoT, including firmware update verification, authentication of sensor data, and protection against Man-in-the-Middle attacks. It also provides a practical example of how the Merkle Root can be used to ensure the data integrity of sensor readings in an IoT device. Furthermore, the blog post addresses the challenges and limitations of implementing the Merkle Root in IoT devices, such as processing power, memory usage, and verification delays, and offers strategies to overcome these obstacles.
Roberto Vazquez
8/18/20243 min read


Introduction
IoT devices are becoming more common in smart homes and industrial applications. Due to their ongoing connection and limited processing and storage, these devices are susceptible to assaults. The Merkle-Root improves device security by maintaining data integrity and verifying information without a central server or complicated infrastructures.
What is the Merkle Root?
The Merkle Root is crucial to cryptography and computer security. It is a cryptographic hash that summarizes Merkle tree data. Merkle trees offer fast and safe verification of big datasets. Each tree leaf node hashes a data block, while the higher nodes have the hashes of their child nodes. The Merkle Root, the top node, ensures data integrity.
Application of the Merkle Root in IoT Devices
IoT devices are usually connected to a network that continuously sends and receives data. In this context, the Merkle Root can be used for:
1. Firmware Update Verification:
Firmware update verification is a crucial Merkle Root IoT application. The update server's Merkle Root lets the IoT device check the firmware before updating. When the firmware's Merkle Root does not match, the update is blocked, preventing malware installation.
2. Authentication of Sensor Data:
IoT devices send sensor data to a hub or cloud for processing. The device may construct a Merkle Root to verify data integrity before transferring it. This Merkle Root allows the receiving center to check that the data was not changed during transmission, assuring its legitimacy.
3. Protection Against Man-in-the-Middle Attacks:
In an IoT system, an attacker might intercept and manipulate device-cloud communication. A Merkle Root lets the device and cloud verify the integrity of communicated data. A Merkle Root discrepancy may indicate a Man-in-the-Middle attack and provide network protection.
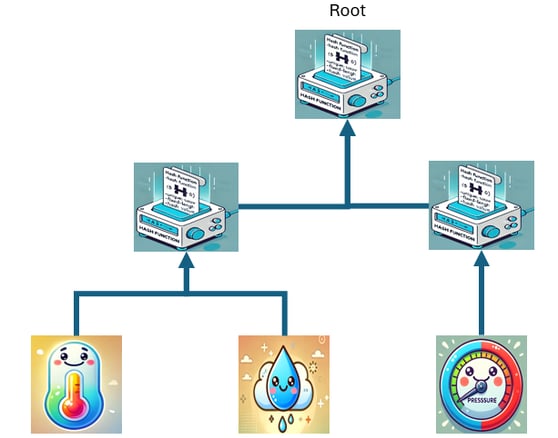
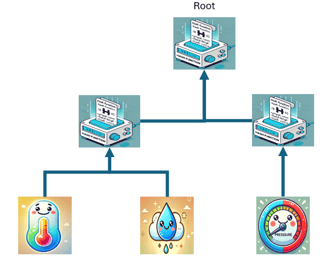
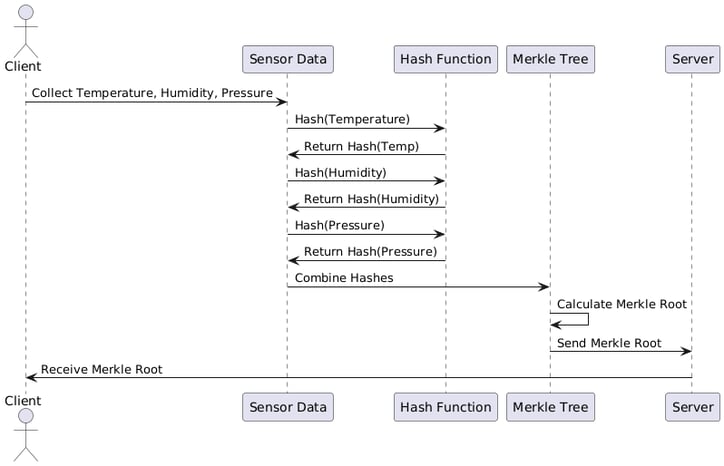
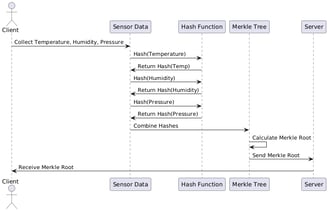
Practical Example in IoT: Data Integrity Verification of Sensors
Consider an IoT gadget that tracks temperature, humidity, and pressure from sensors. We demonstrate a simple Merkle Root verification here:
1. Hash Generation of Sensor Data:
The data collected by the sensors is transformed into individual cryptographic hashes.
2. Construction of the Merkle Tree:
The hashes of the sensor data are combined to form a Merkle tree, and the resulting Merkle Root summarizes all the data.
3. Sending the Merkle Root:
The Merkle Root is sent with the data to the central server or cloud. This server can recalculate the Merkle Root and verify if it matches the one sent, ensuring that the data has not been altered during transmission.
Merkle Root IoT Limitations and Challenges
Despite its benefits for IoT device security, the Merkle Root has certain drawbacks:
IoT devices' low processing capacity makes executing resource-intensive cryptographic techniques like Merkle Roots generation and verification difficult. On low-capacity devices, real-time Merkle Root calculation may slow performance.
2. Memory Usage:
Merkle trees need temporary storage for intermediate hashes. IoT devices with limited memory might struggle to store these values, particularly with vast volumes of data.
3. Update and Synchronization Management:
Managing Merkle Roots consistency and synchronization in dispersed IoT systems is challenging. Recalculating the Merkle Root after every data update might be difficult on several devices.
4. Delay in Verification:
The computation and verification of Merkle Root might cause delays in essential applications requiring fast data verification.
5. Heterogeneous Network Implementation:
IoT devices usually function in networks with diverse capabilities and communication protocols. Implementing a Merkle Root verification system that works across all devices and protocols may need bespoke and complicated technologies.
How to overcome these restrictions
1. Calculation optimisation:
Optimizing low-capacity devices using precomputing hashes or lighter hashing techniques may minimize the processing burden.
2. Storage Efficiency:
Compression or distributed intermediate hash storage may minimize memory use on low-memory systems.
3. Gradual Updates:
Instead of recalculating the whole structure with every bit of data update, the Merkle Roots may be recalculated gradually or in batches to decrease the synchronization and updating effect.
4. Adjustments to Verification
When latency is crucial, hybrid systems may verify only part of the Merkle tree in real-time and process the rest later.
Conclusion: Merkle Root IoT Security
The Merkle Root is critical for IoT data integrity and authenticity. In a continually linked, sensitive world, it offers a quick and safe way to verify that data has not been changed, assuring data dependability and system security.
With the correct tactics, Merkle Roots may improve IoT device security despite technological restrictions. In an increasingly linked world, integrating the Merkle Root into IoT solutions is essential to secure devices and the data they gather and transfer.
Code Explanation: