The Fascinating World of Rainbow Tables in Cybersecurity
Explore the fascinating world of rainbow tables in this comprehensive blog. Delve into what rainbow tables are, how they work, and their pivotal role in password cracking. This post breaks down complex concepts with clear explanations and provides practical Python code examples to illustrate the generation and use of rainbow tables. Whether you're a cybersecurity enthusiast or a professional looking to deepen your understanding, this blog will equip you with the knowledge to appreciate the historical significance of rainbow tables and the modern techniques used to counteract them. Discover the importance of using solid and salted hashes to safeguard sensitive data against evolving hacking strategies.
Roberto Vazquez
9/2/20243 min read


Overview
Safeguarding passwords is of the utmost importance in cybersecurity. Although robust passwords and hashing algorithms provide formidable protection, malevolent individuals consistently devise novel techniques to undermine them. One approach involves the use of rainbow tables. This blog article will explore rainbow tables, their operational mechanisms, and their significance in password cracking. In addition, we will provide Python code examples to reinforce comprehension of these principles.
Define Rainbow Tables.
Rainbow tables are precomputed tables specifically created to decrypt hashed passwords securely. Instead of using brute force, which involves attempting every conceivable password combination, rainbow tables utilize precomputed hash chains to reverse the hashing process optimally. The main objective of a rainbow table is to minimize the algorithmic complexity of password hash cracking by using a comprehensive collection of hash-to-password mappings.
The Operation of Rainbow Tables
Rainbow tables are memory structures that record the results of hash algorithms applied to different plaintext inputs, such as passwords. It was hashing a password, resulting in its conversion into an arbitrary sequence of characters. For example, the password "password123" may be transformed into the following hash value using SHA-256: ef92b778bafe771e89245b89ecbc593feec87dfaaa7d8ae22e5ec37f1d6fbe1d.
A rainbow table would have pre-calculated hashes, such as the one shown, along with their matching plaintext passwords, enabling rapid retrieval and reversal of the hash.
The reduction function
The reduction function is a fundamental element of rainbow tables. This function generates a sequence of hash-to-password mappings by substituting a hash value with a potential plaintext password. Presented below is a condensed summary:
1. Begin by entering a password: "password123"
2. Hash it: ef92b778 ...
3. Utilise a reduction function to provide an alternative password.
4. Perform a hash on the new password.
5. Iterate the procedure to form a chain.
Storage requirements are reduced by storing the resultant chain in the rainbow table with the starting plaintext and the final hash. The hash is compared to the final hashes stored in the table during password cracking. Provided a match is discovered, the sequence is inverted to reveal the initial password.
Sample Python Code: Creating a Basic Rainbow Table
An illustrative Python example will demonstrate the generation and use of a rainbow table for password hash cracking.
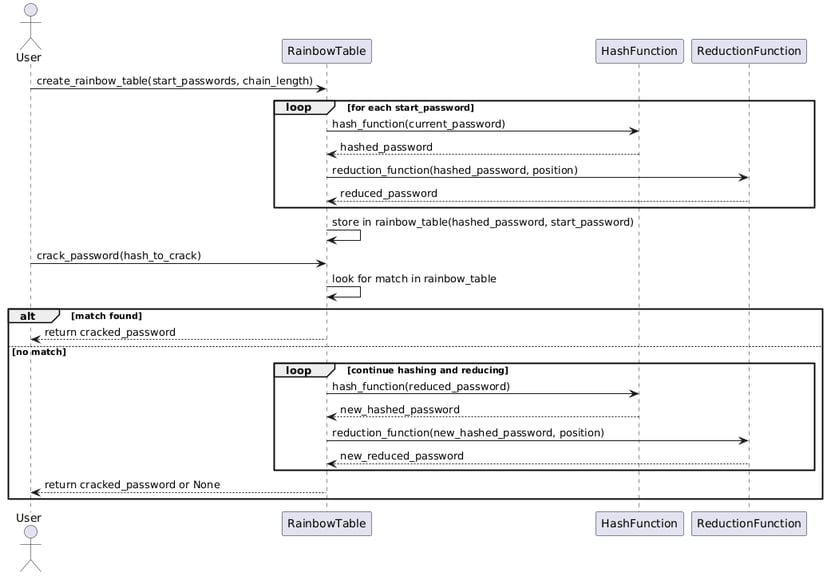
Explanation of the Code
Reduction Function: The reduction_function_dynamic takes a hash and converts it back to a possible plaintext password. This function is a simplified example; real-world reduction functions are more complex and generate unique chains.
Hash Function: The hash_function uses the SHA-256 algorithm to hash a given password.
Rainbow Table Creation: The create_rainbow_table function generates a rainbow table by iterating over a list of starting passwords and creating chains of hashes and reduced passwords.
Cracking a Password: The crack_password function attempts to reverse a given hash by looking it up in the rainbow table and backtracking through the chain.
Limitations and Countermeasures
While rainbow tables are robust, they have limitations. They are only effective against unsalted hashes, where the same password consistently results in the same hash. Modern systems use salting to counteract rainbow table attacks, adding a random value (salt) to each password before hashing. Also, it ensures that even if two users have the same password, their hashes will differ, rendering rainbow tables ineffective.
Conclusion
Rainbow tables are a fascinating and historically significant technique in password cracking. Although advancements like salting have diminished their effectiveness, understanding rainbow tables offers valuable insights into the ongoing battle between cybersecurity defenses and hacking techniques. As exploring cybersecurity, remember the importance of using practical, salted hashes to protect sensitive information.
This blog post provided an in-depth look at rainbow tables, complete with Python code, to illustrate how they are generated and used by understanding these techniques, better equipped to implement robust security measures in systems.
